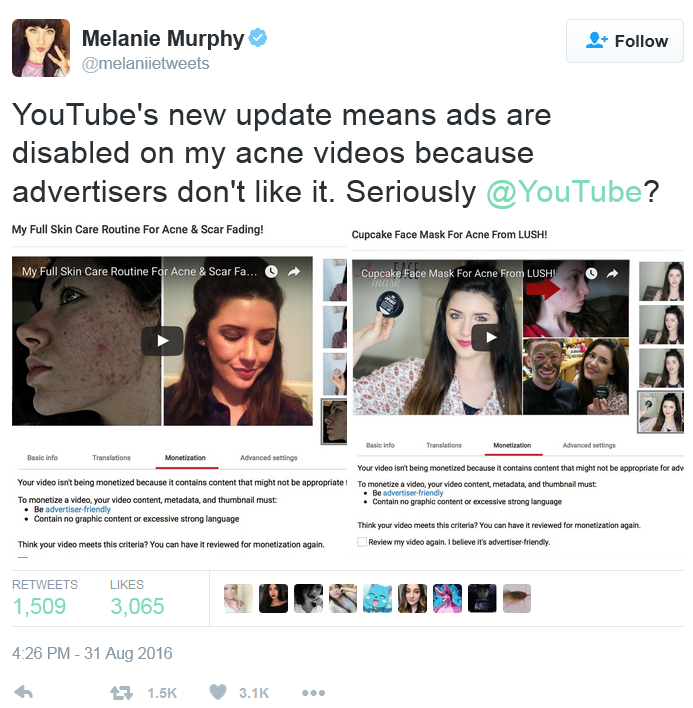
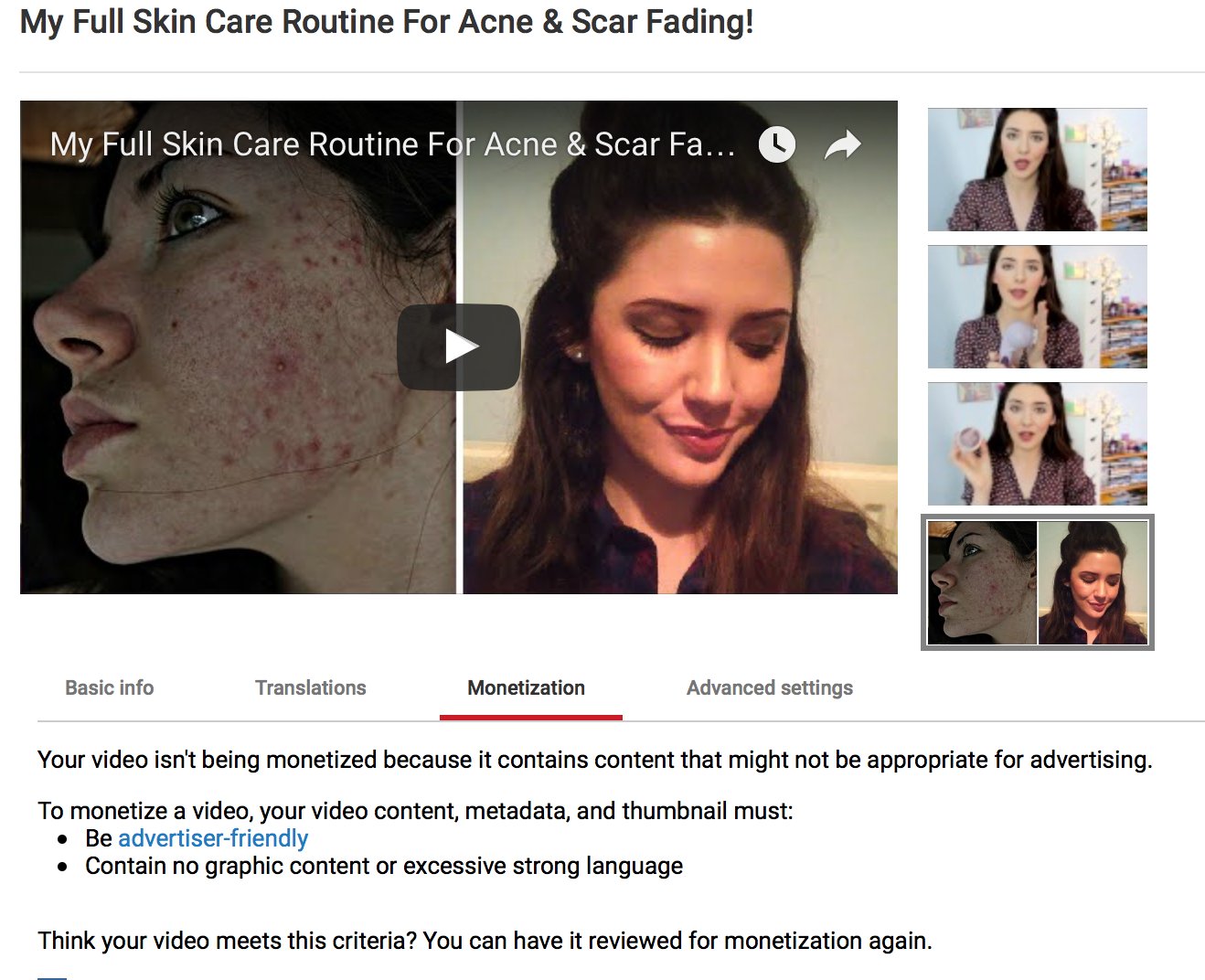
“The Old Man’s Pendant” was a short film I created as a more involved and complex project to teach myself video editing. Prior to that, the only things that I had created were silly five-second joke clips or music videos spliced together from random things I pointed my camcorder at and polished with crude experimentation in visual effects. After my third (and most complicated) music video, I decided it was time to do something with more structure. Inspired by James Rolfe’s “How I Got Started” story and being stuck at home due to the ice and snow on the roads, I came up with nothing more than a crude idea for a short movie and started recording. I’ll spare you the details since I’m planning to make a documentary about my journey in the near future, but the bottom line is that such a small project which I expected to be finished in a few days at the most ended up taking around four months. It was a completely original work from scratch where I was learning not only video editing but writing and music composition. I also learned first-hand just how difficult it really is to put together a high-quality video project.
That movie was shot in January of 2016. One year later, stuck at home and snowed in yet again, I decided that it would be fun to shoot a sequel. My story ideas were better, my footage was more usable with less silly mistakes, and my skill levels had improved significantly. It’s not realistic to finish the post-production work in a week, but surely I could get it done within a month or two, right?
Instead of four months, this one took six months to complete. It’s funny how that works. Today, the sequel to my first short film went up on YouTube.
“The Old Man’s Pendant II” took so long to finish and was worth every bit of time it took. It is by far the most polished and interesting thing I’ve created to date. My least developed filmmaking skill is music composition, yet I’m still listening to my own soundtrack as I type this! The improvement between the films is obvious. While there are still plenty of things that could be polished in the final film, I try to avoid falling too hard into the perfectionist artist trap. At some point you need to stop fidgeting about with your creation, put it out there, and move on to the next big thing.
I’m very proud of my latest short film. I hope that you find it as enjoyable and satisfying as the process of creating it has been for me. I’ll be doing a documentary about my progress from the first film to the completion of the second one, so stay tuned for that.
If you’re still interested, feel free to watch the official trailer for The Old Man’s Pendant II, listen to and download the film’s soundtrack, watch the TOMP2 teaser video, and check out the behind-the-scenes teaser.
These videos are also available at Vidme: The Old Man’s Pendant II, TOMP2 Teaser, TOMP2 Behind the Scenes Teaser.